Though IT configuration management resists standardization, lifecycle improvements and automation, it is a function all businesses must do well. When handled correctly, detailed configuration logs are continuously kept up to date and synchronized across an organization. This provides a way to audit the health of security patches, firewall configurations, device updates and other critical issues across the firm. In an age of constant cybersecurity compromises and liability, maintaining an accurate and secure record of an organization’s technology assets and their configurations becomes a critical part of the risk management and mitigation strategy.
An IT asset manager’s dream may have finally arrived: blockchain can provide a perfect, unalterable record of the entire history of a device.
Let’s consider a particular thorn in the side of IT: managing firewall rules. How many firewall rules are in your environment? Hundreds? Thousands? Tens of thousands? Which rules support applications that are currently running? Which rules are deprecated? And which have been zombie'd after decommissioned applications were taken offline?
According to ISG Research, business leaders see blockchain technology adding value across their organizations with specific value for IT.
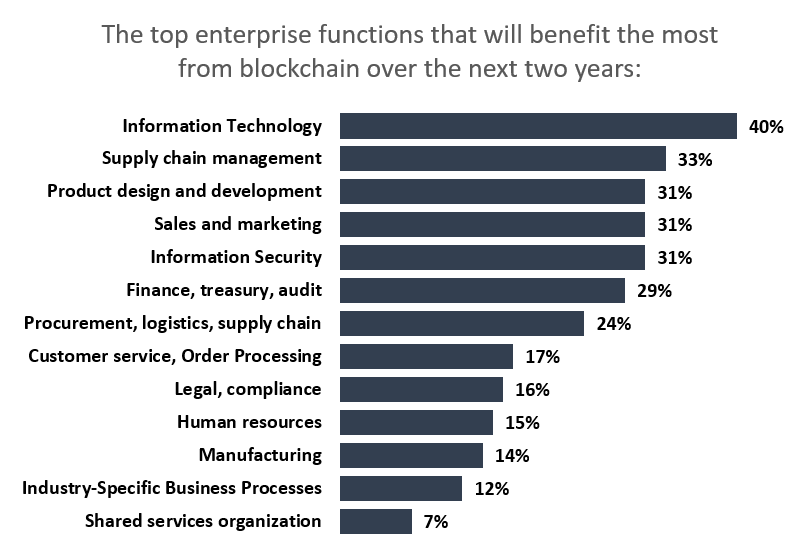
Source: ISG Research Blockchain Survey
Let’s face it, when most enterprises refer to infrastructure lifecycle management, what they usually mean is a set of disconnected processes put in place in an effort to govern the phases of infrastructure lifecycle. And, while many organizations have created strong governance over requests, approvals and deployments, their governance over compliance audits and end-of-life decommissioning can be noncontiguous – leaving a trail of leftover firewall rules. Because blockchain can create a synchronized and distributed source of truth, it has the potential to be an innovative solution for managing the full lifecycle of firewall rules, automatically tracking configuration changes in an audit-friendly, transparent and trusted manner.
First, let’s talk about the basic construct of blockchain as a distributed transaction ledger. As each block of data – in this case representing a configuration change – is added to the chain, it includes a timestamp and a cryptographic hash of the previous block that immutably links the chain. The initial block on the chain contains the deployment of the asset on the network along with all the usual asset management data. Subsequent blocks contain changes to the asset, names of the people who approved them and the applications impacted. Because of the way the blocks are linked cryptographically, it is difficult if not impossible to alter or corrupt previous transactions.
Organizations can automate service management to correlate interrelated blockchains that record transactions according to smart contracts (business rules configured into the blockchain). The added benefit of this approach is recording change management approvals directly into the device ledger.
Every block of data in a blockchain is comprised of many fields, including rule updates, change management approvals, timestamps, and the cryptographic hash of the previous block. The "aha" moment happens when asset managers realize the power of this approach and the inherent security in chaining hashes. Given a set of appropriate infrastructure standards, the integrity of the blockchain itself substantiates compliance with an infrastructure audit.
Why does applying blockchain technology to firewall management matter?
The firewall management use case for blockchain can be extended to every component of infrastructure – including load balancers, switches and routers – which naturally has implications for the current challenges organizations face in feeding data into the configuration management database (CMDB).
The reason so many enterprises presently struggle to build and maintain a real-time CMDB is the shortage of timely validated data sources. Using blockchain’s inbound transaction processing capability to capture approved changes allows an IT organization to create both an audit trail and real-time updates to the CMDB. Typically, a CMDB serves as a database of device metadata contained in configuration item (CI) records, not the actual device configurations. The "gold" copies of configuration files continue to live on devices in production, a fact that runs counter to the goal of the CMDB – and a challenge that blockchain can solve.
When an enterprise needs to know how discreet infrastructure components interconnect to form an application delivery ecosystem, for example, CI relationships are some of the most sought-after data in the CMDB. A blockchain is an ideal solution to enable a CMDB to fulfill its promise as the single source of real-time truth about an enterprise’s entire infrastructure.
Blockchain solutions have emerged, and enterprises should be exploring the potential of the technology. Now is the time to evaluate both open-source and commercially packaged solutions to build organizational knowledge and ease your network management. Contact us to discuss how ISG can help you navigate the blockchain opportunity.
